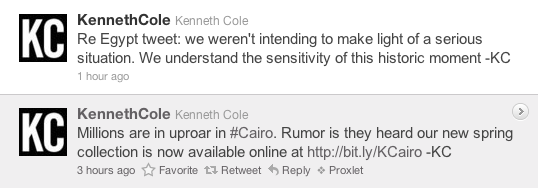
And I like it! But I think that, in a fit of pique, I won’t be buying any more of his clothes. Screenshot against its inevitable disappearance:
Category: Spam
Twitter is creepy
Yesterday I twittered a thing about the prostate cancer vaccine approval and this is what I got in my inbox the next morning.
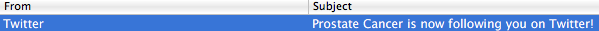
WELL GOOD.
Suggestionbombing
I twitted this, but I think it deserves a fuller exploration. Is it possible to Googlebomb Google’s own search-box completion content via sheer volume of queries? Presumably the things you get are based on search popularity modulated by recentness, which is why typing in “blagojevich go” gives you “-vernor” first followed by “-lden.” That makes sense, but that means it’s also vulnerable to mobbing.
Say I run a company called Adkins AC, selling air conditioners. Getting my site to the top of the results for “air conditioner” is going to be extremely difficult, requiring either a lot of time and work, or a lot of money to SEO spammers whose efforts will eventually get me deranked anyway. I can buy an Adword, but in the summer that’s going to run through my budget pretty fast. Another vector of attack would be to just get a whole lot of people to search for “air conditioner adkins ac,” which is going to put me much closer to the top in the dropdown suggestions.
Now even if I make all my friends and business contacts do that, it’s not really going to affect Google’s giant sample pool. But if I pay a few thousand bucks to somebody who runs a botnet, I could have a million PCs searching for “air conditioner adkins ac” in a randomized, staggered pattern from February to April. By the time things start heating up in May, I’m the first suggestion result, and I’ve probably spent less money than a consistent Adword would cost.
Yes, this is all illegal, but much less detectably so than SEO or email spam. The botnet owners could probably make good money this way too, since you could take on hundreds of customers at a time, and the market for DDOSes-on-demand can’t really be growing that much. Now I’ve fixed the economy! Well, someone’s economy.
I know the Googlebomb wars are kind of a thing of the past, since Google’s gotten much better at deranking targeted efforts to mess with Pagerank, but suggestions are a whole different frontier–and like most frontiers, I’m guessing it’s not well policed.
Got an interesting virus email today, this one claiming to be an invoice from United Airlines for a ticket purchased online. No bad links or anything, and the login it gave was one of my actual addresses; it was only when I saw that the “invoice attachment” was a zip file that I caught on.
Never, ever open zip files that you get in an email. People know that by now, right? It’s 2009.
(And never eat yellow snow. That’s a goodie from 1942. –Kara)
The intent of this post is not actually to lionize Baz Luhrmann in any way
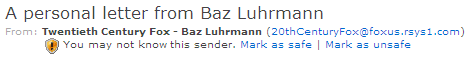
Oh, I know Baz Luhrmann, all right.
Ain’t nobody marking that motherfucker safe.
I got spam today with the most intriguing subject line ever, so I googled it and bam, first result was Gordon Fay’s 24-hour RPG Blood Royal. The subject line, and its description: “A competitive game of fairy-tale intrigue and skulduggery in which players take the roles of a dying King’s children, each vying to be named successor at the end of the week.” How cool is that! Thanks, spam! Welcome to unintended consequences.
Actually, the whistling is optional.
Man, today’s new virus email was pretty cool! The subject line was “You visit illegal websites,” and it was spoofed to appear like it came from “Department@fbi.gov.” Attachment: the standard ZIP file. Little do they know that all the illegal websites I visit are based outside the US, and would fall under the purview of the CIA! AH HA!
Seriously, if you get that or a similar email, don’t open the attachment, don’t open the email, don’t even preview it. Just hit the Junk button in Thunderbird and whistle a merry tune. (You are using Thunderbird, right?)
I think the killer app for Mechanical Turk is already out there. Think about it: what’s very simple for a human, very hard for a computer, shows up everywhere and acts as a gatekeeper from potentially greater value?
That’s right: those little “verify you’re a human” image boxes that make you transcribe a series of bendy, obscured letters and numbers in order to leave a Blogger comment, or get an LJ account or a GMail address. (Less awkwardly, more annoyingly, they’re called CAPTCHAs.) Yoz Grahame pointed out like a year ago that these are a solved problem: you just go to a CAPTCHA page, grab the image, and put it in front of porn on one of your other sites. Step three: profit!
The only problem with that scenario is that, well, there are ways to get porn without all that tiresome thinking, and most porn-seekers will take them over your time-consuming verification step. It’s easier to type BRITTNAY SPEER NUDE into Google Image Search than it is to decipher Ty$23YiD.
But if MT’s model works (and I’m not saying it does; right now only Amazon uses it, and you’d have to work hard and boringly to make five bucks an hour), and if it gets sufficiently popular that the site’s admins won’t notice spammers slipping CAPTCHAS in, this could be a viable crack. Sign up for an account, pay Random Human two cents to verify it, and spam, spam away. It’s okay, say the servers you’re using to link your herbal V1agra incest mortgage. I know that’s not a bot!
CAPTCHAs are the least bad solution to bot-signups out there right now, but I hope the tech startups that are built around providing that kind of authentication don’t get comfortable. They’ve never been more than a stopgap.
Got a fairly clever phishing email today–this one faked all the headers right, and they even spell-checked! I’m impressed (although they still missed a period).
Anyway, if you get something called “Paypal Flagged Account” that appears to be from support@paypal.com, ignore it. The big clue in this one, as always, was the actual URL of the “Click here to verify your Information” link. Always right-click on links like those and hit “Properties” to check where you’re really going.